IT system monitoring
IT system monitoring is a significant tool in IT risk management because it delivers data on the extent and efficiency of system resource use.
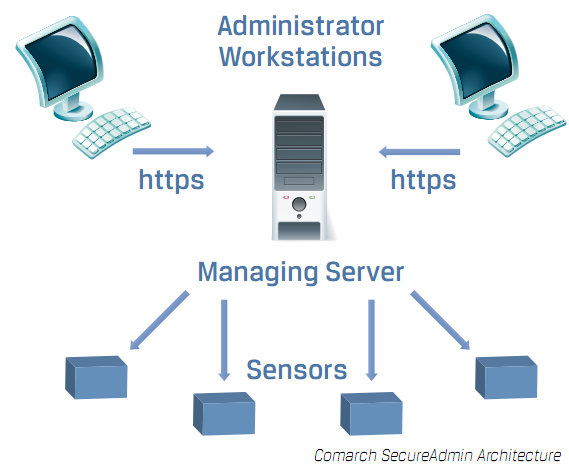
Comarch SecureAdmin is a user activity monitoring system which operates transparently at the network level (passive and active analysis). These features mean that implementing Comarch SecureAdmin does not require the modification or reconfiguration of existing applications or systems and its presence is not visible to users.
A further imposing feature is the capacity to monitor encrypted connections. This makes it an excellent supplementary system for monitoring user activity. It is based on application and system logs and may also be deployed to monitor administrator activity.
Sensors are dedicated servers equipped with at least three network interfaces, including two operating in bridge mode. Their task is to monitor network traffic, analyze selected connections and collect data. There are two ways network traffic is analyzed:
- passively,
- actively (using the Man in The Middle technique).
Passive analysis is based on the incoming packet queue mechanism provided by iptables software. This is the way analyses for simple protocols, in plain text, such as Telnet, POP3, IMAP, FTP, SMTP, HTTP, SMB, NFS, X11, RDP, LDAP, Oracle, MySQL, PostgreSQL and MSSQL are conducted. However, MITM analysis techniques involve a sensor that intervenes between the server and client and assumes their identities. Protocols using encryption or that require modifications to the transmitted packets such as SSH (versions 1 and 2), SSL (FTP, POP3, IMAP, LDAP, SMTP, HTTP), RDP and X11 are analyzed in this way.
Network traffic analysis and monitoring provided by Comarch SecureAdmin is transparent for users. This is easy to achieve with passive analysis because the packets transmitted in the connections are in no way modified. Comarch SecureAdmin is exceptional because it also offers transparency in MITM connection analysis. In this mode the sensor uses iptables mechanisms to transfer connections to a local port and simulate the client’s connection. Meanwhile, the sensor connects with the server in the name of the client. The server hides behind the IP addresses of real servers and clients so that it is invisible both to the client and the server. SSH key and SSL certificate and key management is performed centrally from the administration console.